The Notorious Hacker Group TeamTNT, is officially one of the worst threats to the world of cybersecurity as of late, primarily due to their use of cloud environments for their exploits. Recently, TeamTNT has expanded its activity with a massive campaign where it uses methods based on cloud-native systems for cryptocurrency mining and malware distribution. Their new tactics specifically target Docker and Kubernetes platforms, illustrating how cloud environments are now prime targets for hackers who want to exploit their vast computational resources. This approach not only expands TeamTNT’s capacity to generate revenue but also reflects its adaptability and willingness to change tactics in response to security advances. By implementing various strategies that capitalize on open vulnerabilities in Docker, the Notorious Hacker Group TeamTNT continues to evolve its methods and remains a significant threat to cloud security.
Advanced Cloud Exploits by TeamTNT
TeamTNT has built a reputation for deploying sophisticated techniques that make detection challenging. The Notorious Hacker Group TeamTNT is targeting exposed Docker daemons, giving them unauthorized access to large networks. According to Aqua Security’s director of threat intelligence, Assaf Morag, the Notorious Hacker Group utilizes tools such as Masscan and ZGrab to scan and locate open Docker API endpoints. Once identified, TeamTNT rapidly deploys malware within these containers, primarily for cryptocurrency mining.

Through this tactic, TeamTNT can exploit large computational resources without paying for the infrastructure. This has become preferable to hacking groups because it is covert and lucrative compared to the traditional ransomware model known as cryptojacking. The Hacker Group uses compromised Docker instances once again to demonstrate its capability of compromising a cloud-native structure and bypassing conventional security solutions.
Transition to Sliver C2 Framework by TeamTNT
In its latest campaigns, the Notorious Hacker Group TeamTNT has made a notable shift from its traditional tools to the Sliver Command-and-Control (C2) framework. Previously, TeamTNT used methods like the Tsunami backdoor to maintain control over infected systems, but the new Sliver C2 framework offers enhanced command and control capabilities. This shift indicates TeamTNT’s ongoing adaptation to improve its techniques, making its actions more efficient and harder to detect. Sliver allows the Notorious Hacker Group to implement remote commands with ease, facilitating the deployment of crypto miners and other malicious payloads on Docker environments. The framework also supports anonymous communication, reducing the chances of detection. This strategic move from Tsunami to Sliver demonstrates TeamTNT’s continuous evolution as it develops more advanced ways to carry out crypto-jacking in Docker ecosystems.
Revenue Diversification: From Mining to Server Rentals
The Notorious Hacker Group TeamTNT has diversified its revenue model beyond just cryptocurrency mining. TeamTNT now profits from compromised servers by renting them out to third parties, allowing them to leverage infected infrastructure without actively managing it. By distributing malicious payloads on platforms like Docker Hub, TeamTNT creates a continuous distribution channel for its malware, giving it an expanded network of compromised systems. The computational power of these infected systems is then made available for other cybercriminals to exploit, further monetizing TeamTNT’s operations. This approach of renting out compromised systems marks a new level of sophistication and maturity for the Notorious Hacker Group TeamTNT, as it illustrates how criminal groups are evolving to sustain profitability in an increasingly monitored online environment.
Detection and Impact of TeamTNT’s Attacks
TeamTNT’s latest campaign was first detected when Datadog, a security monitoring service, noticed unusual activity in cloud environments. The Notorious Hacker Group TeamTNT was attempting to create a Docker Swarm from infected instances, allowing them to coordinate resources across multiple compromised Docker containers. This discovery revealed the extensive scope of TeamTNT’s operations, which could affect thousands of cloud-native environments globally.
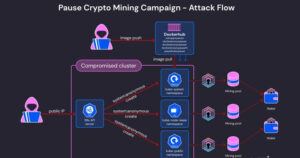
The Notorious Hacker Group TeamTNT poses a heightened threat to industries that rely heavily on cloud platforms, such as finance, healthcare, and retail, where exposed Docker daemons can lead to breaches with devastating consequences. Misconfigurations in Docker containers, particularly with open APIs, have allowed TeamTNT to take control of numerous cloud instances, posing a severe risk to the security of sensitive data stored within these environments.
Security Measures Against TeamTNT
For organizations, defending against the Notorious Hacker Group TeamTNT requires implementing strict security measures that mitigate the vulnerabilities exploited by the group. Aqua Security has suggested that organizations protect Docker APIs and turn off unused cloud services, the access vectors often ignored by cybersecurity officers. Security teams should periodically look at traffic activity in different segments to ensure that there is no unusual activity by an unauthorized user and also use network segmentation to confine the damage of a breach. Organizations must also perform routine assessments to eliminate Docker environments that could potentially allow the Notorious Hacker Group TeamTNT in. These measures are critical in preventing unauthorized access and protecting valuable cloud resources from exploitation.
Emerging Cyber Threats and the Future of TeamTNT
The rise of cloud-native environments has created new opportunities for groups like the Notorious Hacker Group TeamTNT. With their relentless focus on cloud platforms, TeamTNT exemplifies the increasing risk posed by cybercriminal organizations that target cloud services for large-scale, profitable operations.

As more organizations rely on cloud-based infrastructure, the Notorious Hacker Group TeamTNT will likely continue to refine its techniques and seek out new vulnerabilities to exploit. Therefore, staying informed about these evolving threats and implementing robust cloud security practices is essential for any organization looking to defend against the persistent risk posed by TeamTNT.
Conclusion
The Notorious Hacker Group TeamTNT continues to present a significant threat to cloud-based infrastructure through its adaptable and sophisticated approach to cybercrime. By exploiting vulnerabilities in Docker and Kubernetes environments, TeamTNT has managed to sustain large-scale cryptojacking operations and even monetize compromised resources by renting out infected servers. The group’s recent shift to the Sliver C2 framework and use of AnonDNS indicate a calculated effort to evade detection while maximizing their criminal profits.
The continuous vigilance and creativity of the TeamTNT hacking group demonstrate that organizations must remain vigilant and implement recommended best practices when working in cloud-native environments. And, as cloud computing remains a crucial part of today’s organizations more and more often, businesses need not only react to threats and follow measures taken by the hackers but actively protect companies from these actions and regularly change and develop protection measures against such threats like the Notorious Hacker Group TeamTNT.
