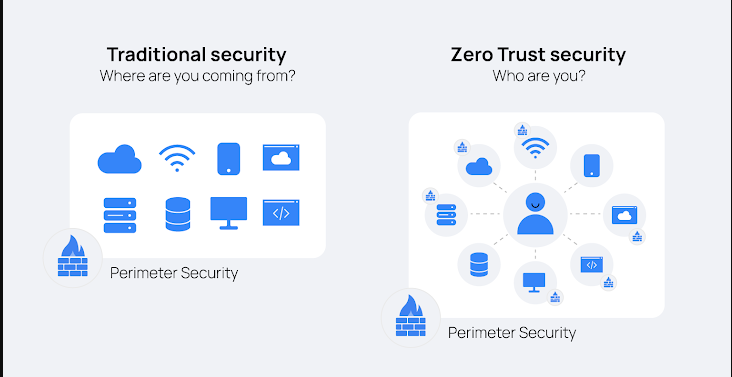
Organizations embrace Zero Trust Security more and more as technology develops. Because they must contend with an ever-increasing array of cyberthreats. Conventional approaches of network security placed complete faith in the network, leaving systems. Open to dangers like compromised credentials or insider assaults. However, the foundation of the Zero Trust Security paradigm is the principle of “trust nothing, verify everything.” According to this method, all access requests—from both internal and external users—must be validated before being granted network access.
The impact of Zero Trust Security on risk management is substantial. Organizations implementing this model enjoy stronger data protections, fewer breaches, and better compliance. It makes sure that only the appropriate individuals have access to sensitive data, improves cybersecurity posture, and lowers unauthorized access. Insider dangers and assaults are becoming more challenging to identify using conventional techniques, but our systematic verification approach reduces their likelihood.
Steps to Apply Zero Trust Security
To establish Zero Trust Security, organizations should implement layered cybersecurity practices that include robust security monitoring, threat detection, and continuous risk evaluation. Here’s how Zero Trust Security works in practical terms:
- Create Robust Authentication: To guarantee strong identity and access management (IAM), use two-factor authentication (MFA) and single- sign-on (SSO). These mechanisms verify every user’s identity, adding an essential layer to Zero Trust Security.
- Network Segmentation: Divide networks into smaller segments, which restrict access to specific areas only for authorized users. This way, a compromised user in one segment cannot move laterally to other sections of the network.
- Behavioral Analysis: Continuously monitor behavior patterns. Security monitoring tools detect deviations from the norm, helping organizations quickly identify potentially malicious actions. Behavioral analysis is a crucial component of Zero Trust Security, as it detects unusual access attempts or file transfers.
- Adaptive Access Controls: Implement dynamic policies that automatically adjust permissions based on context, such as location, device, or time of access. This flexibility reinforces Zero Trust Security by limiting access when suspicious conditions are detected.
Applying Zero Trust Security requires diligent security policies and a proactive approach to threat mitigation. A tool like Wazuh aids in all these areas by automating and centralizing threat detection and incident handling processes.
Leveraging Wazuh for Enhanced Zero Trust Security
Wazuh is an invaluable asset for organizations aiming to strengthen Zero Trust Security because it offers powerful SIEM capabilities and comprehensive security monitoring. Here are some of the ways Wazuh integrates with Zero Trust Security:
- Actual Time Threat Detection: Wazuh’s real-time threat identification capability is just one of its best qualities. It identifies anomalous activity through log analysis, like several unsuccessful login attempts or attempts from unrecognized devices. This real-time detection aligns perfectly with Zero Trust Security, where constant validation is key.
- Event Correlation: Wazuh can correlate security events across the network, linking them to potential attack chains. This feature is particularly useful in cybersecurity since it enables security teams to quickly identify when small, isolated incidents may be part of a larger attack.
- Automated Incident Response: With Wazuh, organizations gain access to automated incident response mechanisms. When a threat is detected, Wazuh can trigger pre-defined actions, such as isolating a compromised device or terminating a risky session. This reduces the time between detection and response, essential for mitigating threats.
Detecting Abused Legitimate Trust Tools
In order to avoid detection, attackers nowadays frequently incorporate trustworthy software and services into their attacks. This strategy, sometimes referred to as “living off the land” attacks, circumvents conventional security measures by gaining illegal access through the use of programs like PowerShell or remote desktop services. Wazuh enhances Zero Trust Security by identifying unusual patterns in these tools’ usage.
Wazuh has the ability to identify unusual activities, such as when an attacker utilizes a legitimate tool, such as PowerShell, to run illegal scripts. Wazuh’s continuous log data analysis helps organizations spot any misuse of legal tools by spotting departures from typical activity.
By identifying hidden risks, this degree of threat detection ensures that enterprises continue to adhere to security policies and regulations, strengthening network security. As these threats often evade standard tools, Wazuh’s ability to recognize such misuse makes it a valuable asset in Zero Trust Security environments.
Detecting Initial Access Attempts
One of the most important aspects of zero trust security is identifying first access attempts. Attackers usually use spear-phishing assaults, weak passwords, and vulnerabilities to establish their initial presence on a network. Wazuh provides ongoing management of vulnerabilities and log evaluation to mitigate this risk.
- Vulnerability Management: Wazuh regularly scans systems and apps to find vulnerabilities. Organizations lower the chance that an attacker will discover an entry point by fixing these flaws.
- Log Analysis: Wazuh tracks login attempts, IP addresses, and session durations to spot unusual behavior indicative of initial access attempts. If Wazuh detects repeated failed login attempts or login attempts from a suspicious IP address, it can automatically alert the security monitoring team, who can then respond promptly.
These proactive measures allow organizations to respond before attackers fully penetrate the network, aligning with Zero Trust Security’s core objective of preventing unauthorized access.
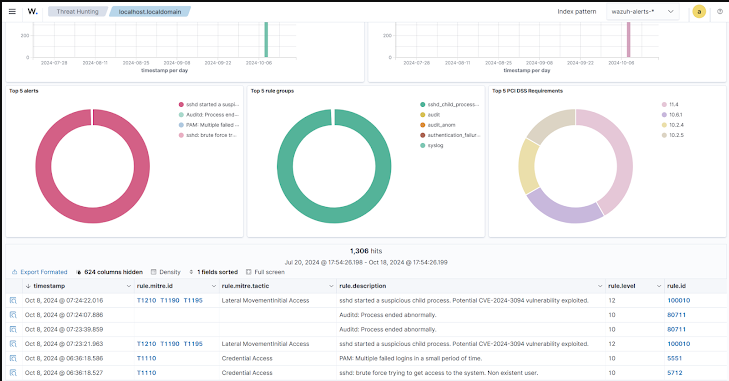
Using Wazuh to Improve Incident Response
A key component of cybersecurity is incident response, and Wazuh is essential in expediting this procedure. In Zero Trust Security, the ability to quickly identify, contain, and respond to incidents is fundamental. Wazuh provides several incident response features that enhance Zero Trust Security:
- Automated Alerts: Wazuh instantly notifies the security team of any anomalies found, enabling them to start a reaction procedure.
- Extensive Forensic Information: Wazuh records extensive information, such as timestamps, source places, and device identifiers, which facilitates post-event analysis. By understanding exactly how an incident unfolded, teams can make improvements to security policies and prevent future attacks.
- Integrated Response Actions: You may set up Wazuh to perform specific tasks automatically, including logging out suspicious users or blocking an IP address. Because it reduces dangers before they become more serious, this kind of incident response is crucial for risk management.
- SIEM Integration: Wazuh’s SIEM features allow it to centralize event data from all over the network, which speeds up incident response times. This comprehensive view enhances data protection and aligns with the Zero Trust Security objective of limiting the potential damage of breaches.
Ensuring Compliance and Data Protection
In addition to securing networks, Zero Trust Security frameworks help organizations maintain regulatory compliance. Regulations like GDPR, HIPAA, and CCPA require organizations to adopt strict data protection measures, especially in sectors handling sensitive personal information. Wazuh assists in maintaining compliance by:
- Generating Compliance Reports: Wazuh automatically creates reports that document security monitoring activities and access controls, proving adherence to regulatory standards.
- Logging Access Data: The log analysis features in Wazuh provide detailed records of access attempts, which are crucial for compliance audits.
- Implementing Policy Enforcement: By enforcing security policies, Wazuh ensures that organizations follow industry best practices, keeping their network security robust.
Through these features, Wazuh strengthens Zero Trust Security by adding a compliance layer that is increasingly necessary in today’s regulatory landscape.
Conclusion
Zero- Trust Safety is not only a recommended practice but also an essential defensive tactic in the ever changing threat landscape of today. Organizations can improve the security of sensitive data, lower vulnerabilities, and adhere to regulations by implementing Zero Trust Security. With features like threat detection, incident response, and thorough security monitoring, Wazuh proves to be a potent tool to support this framework.
