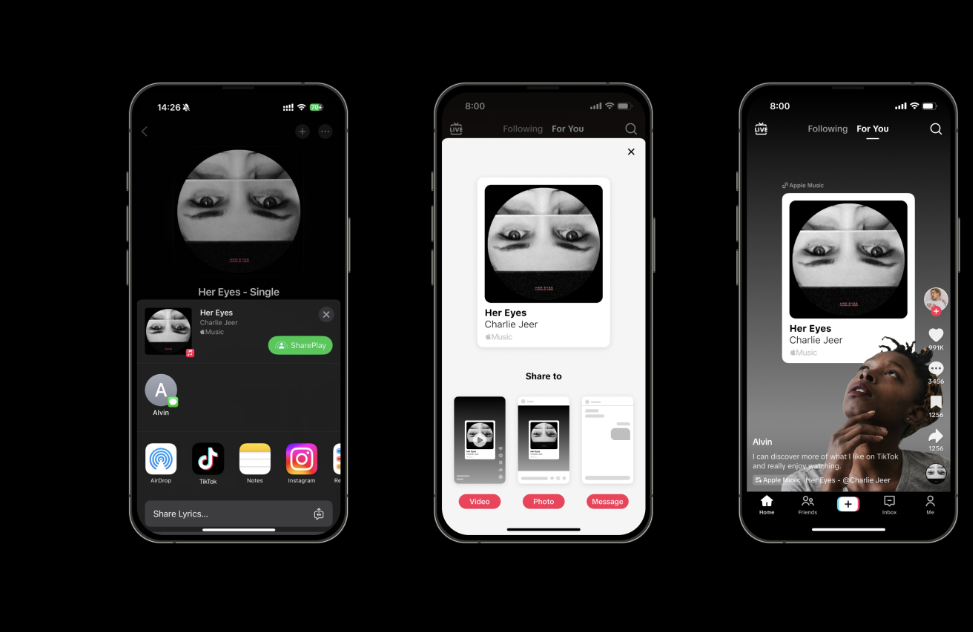
Robotic Delivery: Revolutionizing the Future of Tech-Enabled Logistics
The development of the robot delivery system has forced a change in last-mile delivery systems. Thanks to the use of modern navigation and sensor technologies and AI, robotic delivery startups are creating the proper conditions for increasing the speed of delivery services, minimizing possible risks, and making the delivery process more efficient. This advanced technology … Read more